Nothing up my sleeve numbers posted February 2015
Why does the round constants in sha1 have those specific values?
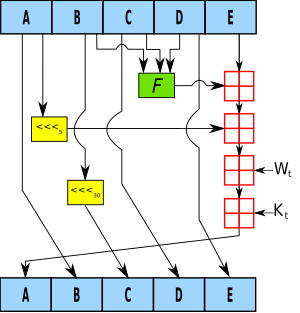
Kt is the round constant of round t;
from SH1-1 - Wikipedia:
The constant values used are chosen to be nothing up my sleeve numbers: the four round constants k are 230 times the square roots of 2, 3, 5 and 10. The first four starting values for h0 through h3 are the same with the MD5 algorithm, and the fifth (for h4) is similar.
from Nothing up my sleeve number:
In cryptography, nothing up my sleeve numbers are any numbers which, by their construction, are above suspicion of hidden properties. They are used in creating cryptographic functions such as hashes and ciphers. These algorithms often need randomized constants for mixing or initialization purposes. The cryptographer may wish to pick these values in a way that demonstrates the constants were not selected for a nefarious purpose, for example, to create a backdoor to the algorithm. These fears can be allayed by using numbers created in a way that leaves little room for adjustment. An example would be the use of initial digits from the number π as the constants. Using digits of π millions of places into its definition would not be considered as trustworthy because the algorithm designer might have selected that starting point because it created a secret weakness the designer could later exploit.


Comments
Maxime
It's not always sufficient to pick a nothing up my sleeve numbers.
Those constants never raised serious concern for the symmetric crypto primitives because in this cas, introducing a trap seems extremely hard ... but it's not anymore the case for asymmetric crypto ... think of the infamous Dual-EC-DRBG.
https://eprint.iacr.org/2014/571.pdf
david
Maxime: in the case of Dual EC, the two values P and Q are not NUMP values
Maxime
David : You are perfectly right ! But what I mean is, you have to be very careful with the use of NUMP in asymmetric crypto.
Keep going with your blog .... I like reading your post !
david
Ah yeah sorry, you mean it's easy to find values that creates a backdoor _and_ are generated as NUMS? I should really read that badass paper :)
leave a comment...